Another annoying by-product of our increasing reliance on electronic communications is unwanted bulk email. Sometimes merchants do not want to bother with targeted marketing. They want to send their email advertising to as many end users as possible, hoping that someone is interested in their product or service. This widely distributed approach to marketing on the Internet is called spam. One of the ways that spam can be sent is by using a botnet or bot.
Bot is derived from the word robot, which describes how the devices act when they are infected. Malicious bot software infects a host, usually through an email or web page link, by downloading and installing a remote control function. When infected, the “zombie” computer contacts servers managed by the botnet creator. These servers act as a command-and-control (C&C) center for an entire network of compromised devices, which is called a botnet. Infected machines can often pass the software to other unprotected devices in their network, increasing the size of the botnet. Some botnets include many thousands of infected devices.
Bot software programs can also cause security issues on the infected machines. The reason is that the installed software may include the ability to log keystrokes, gather passwords, capture and analyze packets, gather financial information, launch DoS attacks, and relay spam. Bots take advantage of time zones, often waking up zombie systems during the idle times in each time zone. Many users keep their computers always connected to the Internet, even when they are away from home or sleeping. This creates the perfect environment for botnet creators to use the bandwidth and processing power of the idle devices.
Figure 15-4 shows an example of how spam is propagated.
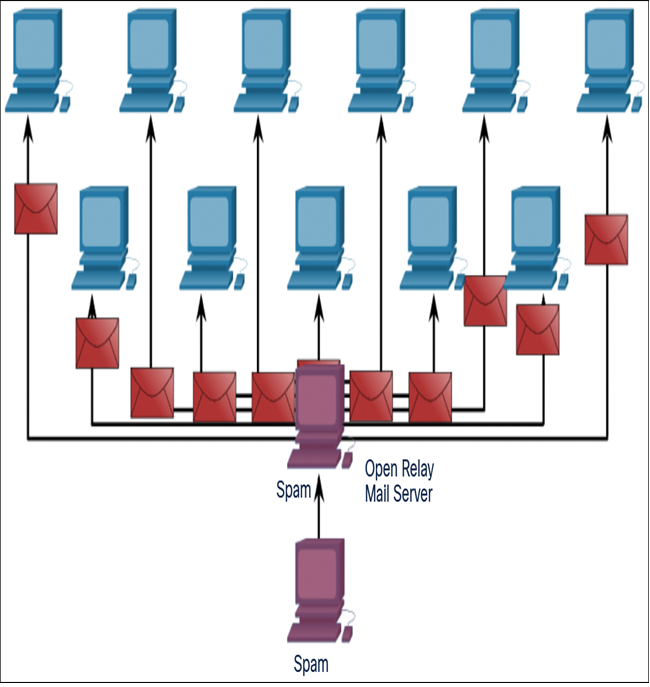
Figure 15-4 C&C Computer Sending Command to Botnet to Spread Spam
Denial-of-Service Attacks (15.4)
Sometimes the goal of a threat actor is to shut down the normal operations of a network. This is known as a denial-of-service, or DoS, attack.
Denial of Service (15.4.1)
Denial-of-service (DoS) attacks are aggressive attacks on an individual computer or groups of computers with the intent to deny services to intended users. DoS attacks can target end-user systems, servers, routers, and network links.
DoS attacks are relatively simple and can be initiated by an unskilled threat actor. The threat actor uses a DoS attack to perform these functions:
- Flood a network, host, or application with traffic to prevent legitimate network traffic from flowing.
- Disrupt connections between a client and server to prevent access to a service.
There are several types of DoS attacks. Security administrators need to be aware of the types of DoS attacks that can occur and ensure that their networks are protected. These are two common DoS attacks:
- SYN (synchronous) flooding—In this attack, a flood of packets is sent to a server requesting a client connection. The packets contain invalid source IP addresses. The server becomes occupied trying to respond to these fake requests and therefore cannot respond to legitimate ones.
- Ping of death—In this attack, a packet that is greater in size than the maximum allowed by IP (65,535 bytes) is sent to a device. This can cause the receiving system to crash. Since 1998, the ping of death is no longer an issue because operating systems now mitigate this attack.
Figure 15-5 shows a DoS attack.
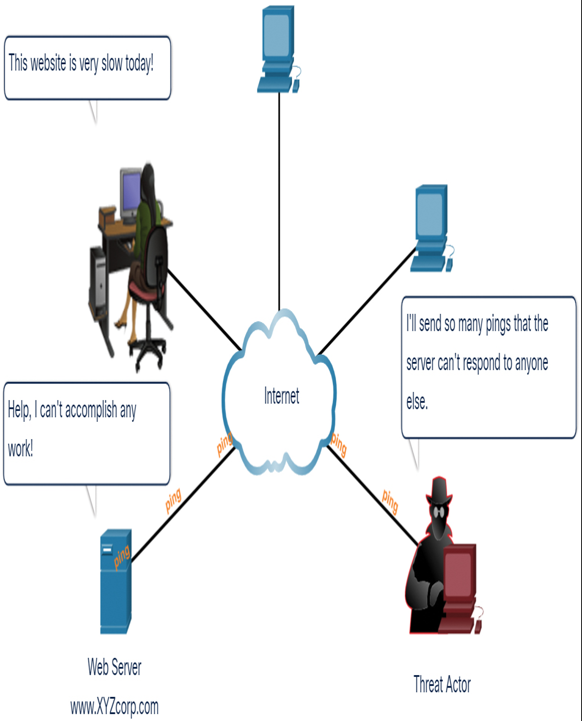
Figure 15-5 A DoS Attack
Distributed Denial of Service (15.4.2)
DoS attacks that come from a single IP address can disrupt a website for a period of time until the attack can be isolated and defended against. More sophisticated types of attacks can bring web services offline for much longer.
Distributed denial of service (DDoS) is a more sophisticated and potentially damaging form of DoS attack. It is designed to saturate and overwhelm network links with useless data. DDoS operates on a much larger scale than DoS attacks. Typically, hundreds or thousands of attack points attempt to overwhelm a target simultaneously. The attack points may be unsuspecting computers that have been previously infected by the DDoS code. The systems that are infected with the DDoS code attack the target site when invoked. This group of infected computers is often called a botnet.
Figure 15-6 shows an example of a DDoS attack.
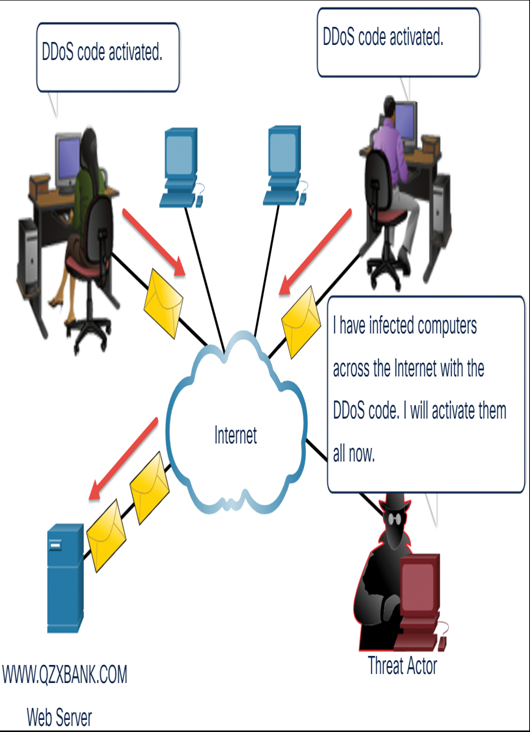
Figure 15-6 A DDoS Attack
Brute Force (15.4.3)
Not all attacks that cause network outages are specifically DoS attacks. A brute-force attack is another type of attack that may result in denial of services.
With brute-force attacks, a fast computer is used to try to guess passwords or to decipher an encryption code. The attacker tries a large number of possibilities in rapid succession to gain access or crack the code. Brute-force attacks can cause a denial of service due to excessive traffic to a specific resource or by locking out user accounts.

