TCP and UDP use port numbers. Port numbers indicate a network process or service from the perspective of both the source of the message and the destination.
Video—Transport Layer Port Numbers (11.3.1)
Refer to the online course to view this video.
TCP and UDP Port Numbers (11.3.2)
In the course of a day, you access many services through the Internet. DNS, web, email, FTP, IM, and VoIP are just some of these services that are provided by client/server systems around the world. These services may be provided by a single server or by several servers in large data centers.
When a message is delivered using either TCP or UDP, the protocols and services requested are identified by a port number, as shown in Figure 11-5. A port is a numeric identifier within each segment that is used to keep track of specific conversations between a client and server. Every message that a host sends contains both a source and destination port.
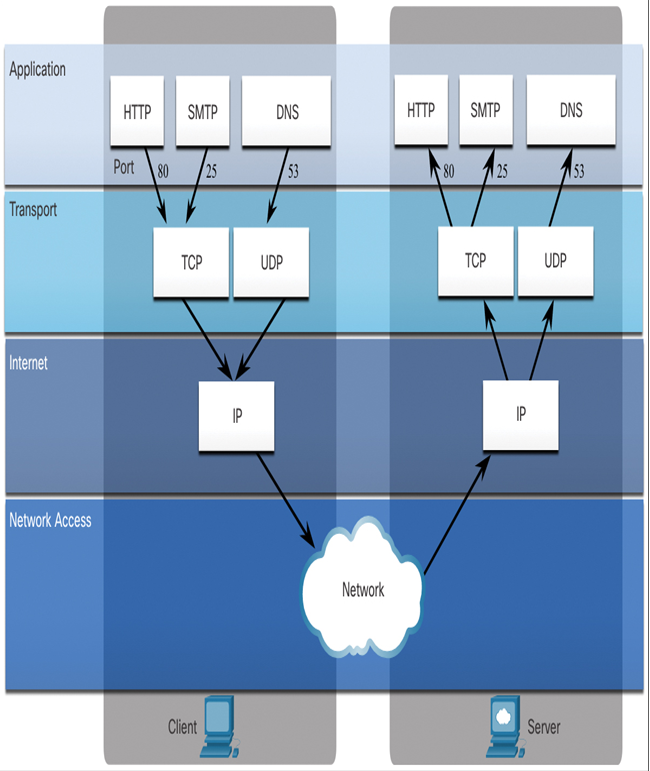
Figure 11-5 Port Numbers Identify the Application in Use
When a server receives a message, the server needs to be able to determine which service the client is requesting. Clients are preconfigured to use a destination port that is registered on the Internet for each service. An example is web browser clients that are preconfigured to send requests to web servers using port 80, the well-known port for HTTP web services.
Ports are assigned and managed by an organization known as the Internet Corporation for Assigned Names and Numbers (ICANN). Ports are broken into three categories and range in number from 1 to 65,535:
- Well-known ports—Destination ports that are associated with common network applications are identified as well-known ports. These ports are in the range of 1 to 1023.
- Registered ports—Ports 1024 through 49,151 can be used as either source or destination ports. They can be used by organizations to register specific applications such as IM applications.
- Private ports—Ports 49,152 through 65,535 are often used as source ports. These ports can be used by any application.
Table 11-2 displays some common well-known port numbers and their associated applications.
Table 11-2 Well-Known Port Numbers and Applications
| Port Number | Transport | Application Protocol |
| 20 | TCP | File Transfer Protocol (FTP)—Data |
| 21 | TCP | File Transfer Protocol (FTP)—Control |
| 22 | TCP | Secure Shell (SSH) |
| 23 | TCP | Telnet |
| 25 | TCP | Simple Mail Transfer Protocol (SMTP) |
| 53 | UDP, TCP | Domain Name Service (DNS) |
| 67 | UDP | Dynamic Host Configuration Protocol (DHCP)—Server |
| 68 | UDP | Dynamic Host Configuration Protocol—Client |
| 69 | UDP | Trivial File Transfer Protocol (TFTP) |
| 80 | TCP | Hypertext Transfer Protocol (HTTP) |
| 110 | TCP | Post Office Protocol version 3 (POP3) |
| 143 | TCP | Internet Message Access Protocol (IMAP) |
| 161 | UDP | Simple Network Management Protocol (SNMP) |
| 443 | TCP | Hypertext Transfer Protocol Secure (HTTPS) |
Some applications may use both TCP and UDP. For example, DNS uses UDP when clients send requests to a DNS server. However, communication between two DNS servers always uses TCP.
Search the IANA website for port registry to view the full list of port numbers and associated applications.
Destination and Source Port Numbers (11.3.3)
The source port number is associated with the originating application on the local host. The destination port number is associated with the destination application on the remote host.
Source Port
The source port number is dynamically generated by the sending device to identify a conversation between two devices. This process allows multiple conversations to occur simultaneously. It is common for a device to send multiple HTTP service requests to a web server at the same time. Each separate HTTP conversation is tracked based on the source ports.
Destination Port
The client places a destination port number in the segment to tell the destination server what service is being requested, as shown in Figure 11-6. For example, when a client specifies port 80 in the destination port, the server that receives the message knows that web services are being requested. A server can offer more than one service simultaneously, such as web services on port 80 at the same time that it offers FTP connection establishment on port 21.
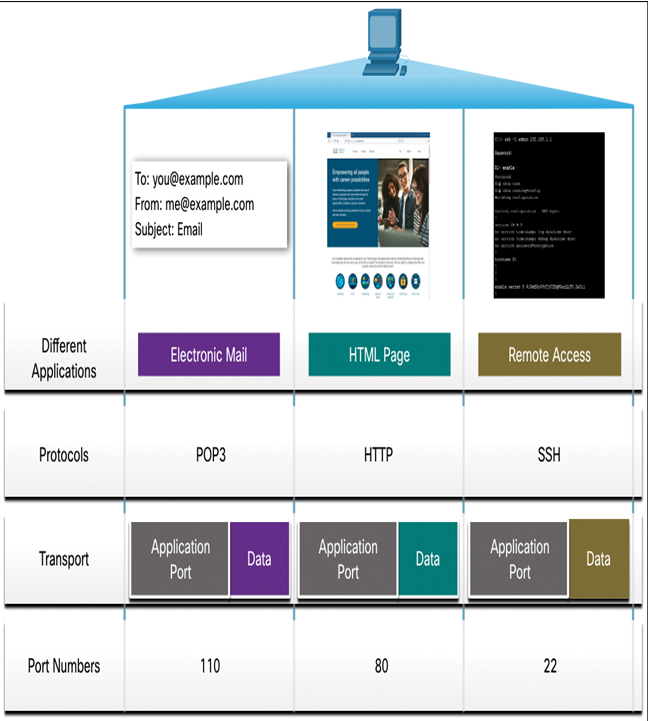
Figure 11-6 A Computer Using Multiple Applications
Socket Pairs (11.3.4)
The source and destination ports are placed within the segment. The segments are then encapsulated within an IP packet. The IP packet contains the IP address of the source and destination. The combination of the source IP address and source port number, or the destination IP address and destination port number, is known as a socket.
In Figure 11-7, the PC is simultaneously requesting FTP and web services from the destination server.
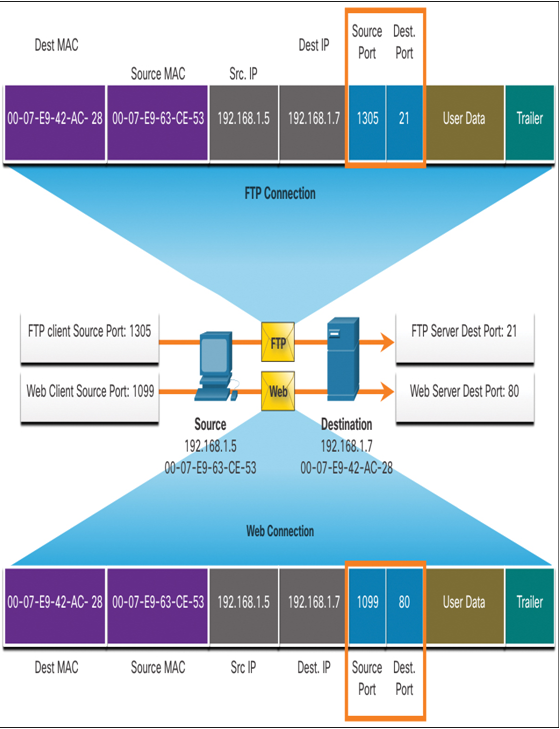
Figure 11-7 A Client and Server Use Port Numbers to Simultaneously Track FTP and Web Traffic
In Figure 11-7, the FTP request generated by the PC includes the Layer 2 MAC addresses and the Layer 3 IP addresses. The request also identifies the source port number 1305 (dynamically generated by the host) and destination port, identifying the FTP services on port 21. The host also has requested a web page from the server using the same Layer 2 and Layer 3 addresses. However, it is using the source port number 1099 (dynamically generated by the host) and destination port identifying the web service on port 80.
The socket is used to identify the server and service being requested by the client. A client socket might look like this, with 1099 representing the source port number: 192.168.1.5:1099.
The socket on a web server might be 192.168.1.7:80.
Together, these two sockets combine to form a socket pair: 192.168.1.5:1099, 192.168.1.7:80.
Sockets enable multiple processes, running on a client, to distinguish themselves from each other, and multiple connections to a server process to be distinguished from each other.
The source port number acts as a return address for the requesting application. The transport layer keeps track of this port and the application that initiated the request so that when a response is returned, it can be forwarded to the correct application.

