Many wireless routers designed for home use have an automatic setup utility that can be used to configure the basic settings on the router. These utilities usually require a PC or laptop to be connected to a wired port on the router. If no device that has a wired connection is available, you might need to configure the wireless client software on the laptop or tablet first.
First Time Setup (13.5.1)
To connect to the router using a wired connection, plug an Ethernet patch cable into the network port on the computer. Plug the other end into a LAN port on the router. Do not plug the cable into the port or interface that is labeled “Internet.” The Internet port connects to the DSL or cable modem. Some home routers may have a built-in modem for Internet connections. If this is the case, verify that the type of connection is correct for your Internet service. A cable modem connection has a coaxial terminal to accept a BNC-type connector. A DSL connection has a port for a telephone-type cable, usually an RJ-11 connector.
After you confirm that the computer is connected to the network router and the link lights on the NIC indicate a working connection, the computer needs an IP address. Most network routers are set up so that the computer receives an IP address automatically from a local DHCP server automatically configured on the wireless router. If the computer does not have an IP address, check the router documentation and configure the PC or tablet with a unique IP address, subnet mask, default gateway, and DNS information.
Design Considerations (13.5.2)
Before entering the configuration utility or manually configuring the router through a web browser, you should consider how your network will be used. You do not want to configure the router and have that configuration limit what you are able to do on the network, nor do you want to leave your network unprotected.
- What should my network be called?—If SSID broadcasting is on, all wireless clients within your signal range will see the SSID name. Many times the SSID gives away too much information about the network to unknown client devices. It is not a good practice to include the device model or brand name as part of the SSID. Wireless devices have default settings that are easy to find on the Internet, as well as known security weaknesses.
- What types of devices will attach to my network?—Wireless devices contain radio transmitters/receivers that function within a specific frequency range. If a device has the necessary radio only for 802.11 b/g, it will not connect if the wireless router or access point is configured to accept only 802.11n or 802.11ac standards. If all devices support the same standard, the network will work at its optimum speed. If you have devices that do not support the n or ac standards, you will have to enable legacy mode. A legacy mode wireless network environment varies between router models but can include a combination of 802.11a, 802.11b, 802.11g, 802.11n, and 802.11ac. This environment provides easy access for legacy devices that need a wireless connection.
Figure 13-11 shows a wireless setup screen.
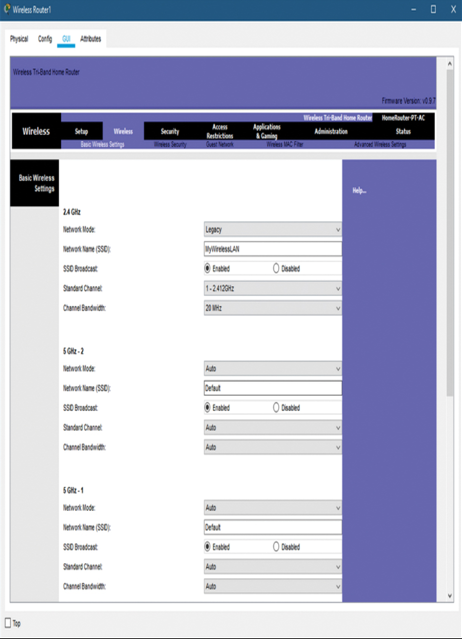
Figure 13-11 Packet Tracer WLAN Configuration Example
Note
Some wireless routers may label legacy mode as mixed mode.
MAC Address Filtering (13.5.3)
The decision regarding who can access your home network should be determined by how you plan to use the network. Many routers support MAC address filtering. As shown in Figure 13-12, MAC address filtering enables you to specifically identify who is allowed on the wireless network. For example, the two top devices are allowed to connect, but the device at the lower right of Figure 13-12 is not. You would have to add the MAC address of the lower-right device so it could connect to the network. It is important to note that MAC address filtering does not provide actual network security. Network security is provided by a firewall or similar device.
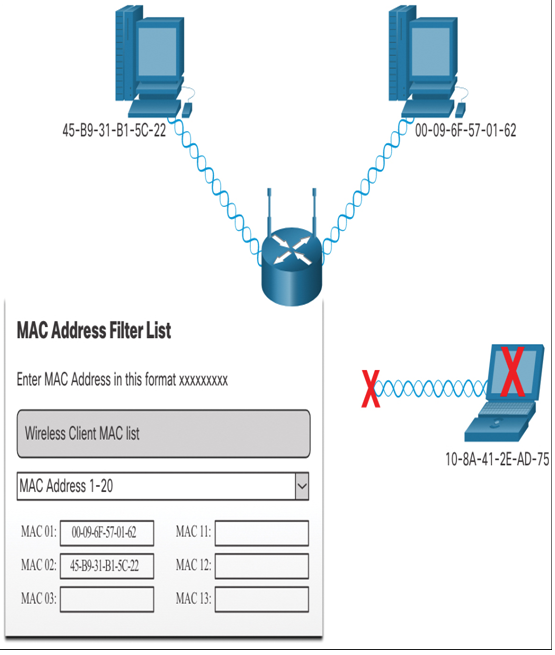
Figure 13-12 MAC Address Filtering
MAC address filtering makes the access to the wireless network more secure, but it also reduces the flexibility when connecting new devices. As an example, if you want to allow any of your friends and family to access the network from any device, it would be difficult and time consuming to configure MAC address filtering on the router.
On some wireless routers, it is possible to set up guest access. This is a special SSID coverage area that allows open access but restricts that access to using the Internet only. Devices on the protected LAN are not accessible to guest users. Not all wireless routers support this function. Research the website of the router vendor to determine if you can create a guest SSID on your model router.
If there is no guest mode on the router, you must restrict who can authenticate with the router to use the services. Authentication methods on wireless routers require a password or passphrase to connect to the SSID. The combination of nonbroadcast SSID and a passphrase ensures that your guests will need information from you to be able to access your network.
Video—Typical Home Network Setup (13.5.4)
Refer to the online course to view this video.
Lab—Configure a Wireless Router and Client (13.5.5)
In this lab, you will complete the following objectives:
- Configure basic settings on a wireless router.
- Connect a wireless client.
Summary (13.6)
The following is a summary of each topic in the chapter:
- Home Network Basics—A home network is a small LAN with devices that usually connect to an integrated router and to each other. The router is connected to the Internet and is likely to be equipped with both wired and wireless capabilities. Many different types of devices might be connecting to a home network. Small business and home routers typically have two primary types of ports: Ethernet ports and the Internet port.
In addition to the wired ports, many home routers include a wireless antenna and a built-in wireless access point. By default, the wireless devices are on the same local network as the devices that are physically plugged into the LAN switch ports. In the default configuration, the Internet port is the only port that is on a different network.
- Network Technologies in the Home—Wireless technologies use electromagnetic waves to carry information between devices. The electromagnetic spectrum includes radio and television broadcast bands, visible light, X-rays, and gamma rays. Each of these has a specific range of wavelengths and associated energies.
The wireless technologies most frequently used in home networks are in the unlicensed 2.4 GHz and 5 GHz frequency ranges. Bluetooth uses the 2.4 GHz band. It is limited to low-speed, short-range communications, but has the advantage of communicating with many devices at the same time. Other technologies that use the 2.4 GHz and 5 GHz bands are the modern wireless LAN technologies that conform to the various IEEE 802.11 standards. Unlike Bluetooth, they transmit at a much higher power level, which gives them a greater range and improved throughput.
Ethernet uses a suite of protocols that allow network devices to communicate over a wired LAN connection. An Ethernet LAN can connect devices using many different types of wiring media. Other technologies, such as powerline, can distribute wired connectivity throughout the premises.
- Wireless Standards—The IEEE 802.11 standard governs the WLAN environment. Amendments to the IEEE 802.11 standard describe characteristics for different standards of wireless communications. Wireless standards for LANs use the 2.4 GHz and 5 GHz frequency bands. Collectively, these technologies are referred to as Wi-Fi.
Wireless routers using the 802.11 standards have multiple settings that have to be configured. These settings include Network Mode, Network Name (SSID), Standard Channel, and SSID Broadcast.
- Wireless Traffic Controls—Wireless devices that transmit over the same frequency range create interference in a Wi-Fi network. This interference can slow down the Wi-Fi performance and potentially break network connections. Channels are created by dividing up the available RF spectrum.
Within a wireless LAN, the lack of well-defined boundaries makes it impossible to detect if collisions occur during transmission. Therefore, it is necessary to use an access method on a wireless network that ensures collisions do not occur. CSMA/CA creates a reservation on the channel for a specific conversation between devices. While a reservation is in place, no other device may transmit on the channel; thus, possible collisions are avoided.
- Set Up a Home Router—To connect to the router using a wired connection, plug an Ethernet patch cable into the network port on the computer and plug the other end into a LAN port on the router. The Internet port connects to the DSL or cable modem. A cable modem connection has a coaxial terminal to accept a BNC-type connector. A DSL connection has a port for a telephone-type cable, usually an RJ-11 connector.
After confirmation that the computer is connected to the network router and the link lights on the NIC indicate a working connection, the computer needs an IP address. Most network routers are set up so that the computer receives an IP address automatically from a local DHCP server.
If SSID broadcasting is on, all wireless clients within your signal range will see the SSID name. It is not a good practice to include the device model or brand name as part of the SSID. Wireless devices have default settings that are easy to find on the Internet.
Wireless devices contain radio transmitters/receivers that function within a specific frequency range. If a device has the necessary radio only for 802.11 b/g, it will not connect if the wireless router or access point is configured to accept only 802.11n or 802.11ac standards. If all devices support the same standard, the network will work at its optimum speed. If you have devices that do not support the n or ac standards, you will have to enable mixed mode. A mixed mode wireless network environment varies between router models but can include a combination of 802.11a, 802.11b, 802.11g, 802.11n, and 802.11ac.
Many routers support MAC address filtering. This makes the wireless network more secure, but it also reduces the flexibility when connecting new devices. On some wireless routers, it is possible to set up guest access. This is a special SSID coverage area that allows open access but restricts that access to using the Internet only. Devices on the protected LAN are not accessible to guest users. Authentication methods on wireless routers require a password or passphrase to connect to the SSID. The combination of nonbroadcast SSID and a passphrase ensures that your guests will need information from you to be able to access your network.

