Pretexting is a form of social engineering where an invented scenario (the pretext) is used to get the victim to release information or perform an action. The target is typically contacted over the telephone. For pretexting to be effective, the attacker must be able to establish legitimacy with the intended target, or victim. This often requires some prior knowledge or research on the part of the attacker. For example, if a threat actor knows the Social Security number of the target, the threat actor may use that information to gain the trust of the target. The target is then more likely to release further information.
Phishing
Phishing is a form of social engineering in which the phisher pretends to represent a legitimate person from another organization. The phisher typically contacts the target individual via email, as shown in Figure 15-3, or text message. The phisher might ask for verification of information, such as passwords or usernames, to prevent some terrible consequence from occurring.
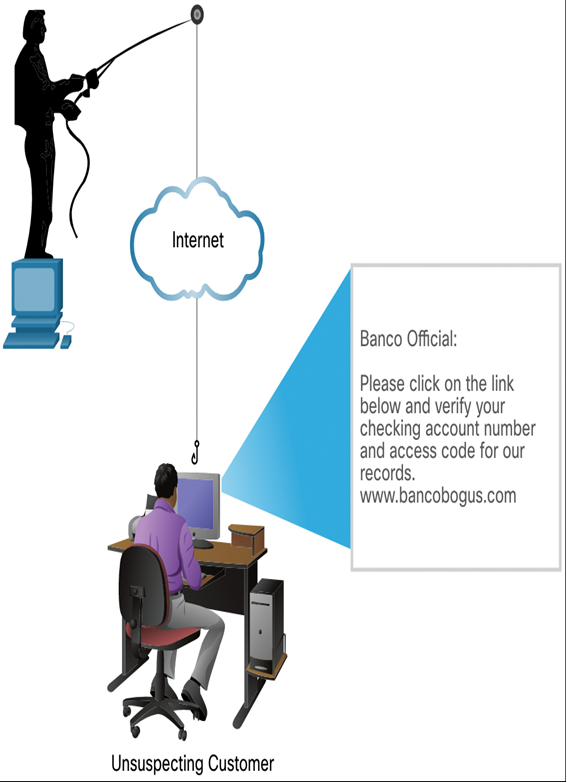
Figure 15-3 A Phishing Attack
Vishing/Phone Phishing
A new form of social engineering that uses voice over IP (VoIP) is known as vishing. With vishing, unsuspecting users are sent a voicemail instructing them to call a number that appears to be a legitimate telephone-banking service. The call is then intercepted by a thief. Bank account numbers or passwords entered over the phone for verification are then stolen.
Lab—Social Engineering (15.2.3)
In this lab, you will research examples of social engineering and identify ways to recognize and prevent it.
Malware (15.3)
In addition to social engineering, other types of attacks launched by malicious software exploit the vulnerabilities in computer software. Malware is the short name for malicious software.
Malicious Software (15.3.1)
Examples of malware attacks include viruses, worms, and Trojan horses. All of these types of malware are introduced onto a host. They can damage a system, destroy data, as well as deny access to networks, systems, or services. They can also forward data and personal details from unsuspecting PC users to criminals. In many cases, they can replicate themselves and spread to other hosts connected to the network. Imagine how difficult it would be to re-create saved files, such as game files, license key files, photographs, and videos.
Sometimes these techniques are used in combination with social engineering to trick an unsuspecting user into executing the attack.
Types of Malware (15.3.2)
Malware attacks are introduced onto a host through emails, texts, Bluetooth connection, and other means. Malware can be used to steal sensitive information, allow unauthorized access to system resources, and create problems connecting to networks.
Viruses
A virus is a program that spreads by modifying other programs or files. A virus cannot start by itself; it needs to be activated. When activated, a virus may do nothing more than replicate itself and spread. Though simple, even this type of virus is dangerous because it can quickly use all available memory and bring a system to a halt. A more serious virus may be programmed to delete or corrupt specific files before spreading. Viruses can be transmitted via email, downloaded files, and instant messages, or via CD or USB devices.
Worms
A worm is similar to a virus, but unlike a virus, it does not need to attach itself to an existing program. A worm uses the network to send copies of itself to any connected hosts. Worms run independently and spread quickly. They do not necessarily require activation or human intervention. Self-spreading network worms can have a much greater impact than a single virus and can infect large parts of the Internet quickly.
Trojan Horses
A Trojan horse is a program that is written to appear like a legitimate program when, in fact, it is an attack tool. It cannot replicate itself. A Trojan horse relies on its legitimate appearance to deceive the victim into initiating the program. It may be relatively harmless or may contain code that can damage the hard drive content of the computer. Trojans can also create a back door into a system that then allows threat actors to gain access.
Spyware (15.3.3)
Not all attacks do damage or prevent legitimate users from having access to resources. Many threats are designed to collect information about users that can be used for advertising, marketing, and research purposes. They include spyware, tracking cookies, adware, and popups. While these may not damage a computer, they invade privacy and can be annoying.
Spyware
Spyware is any program that gathers personal information from your computer without your permission or knowledge. This information is sent to advertisers or others on the Internet and can include passwords and account numbers.
Spyware is usually installed unknowingly when downloading a file, installing another program, or clicking a popup. It can slow down a computer and make changes to internal settings, thus creating more vulnerabilities for other threats. In addition, spyware can be very difficult to remove.
Tracking Cookies
Cookies are a form of spyware but are not always bad. They are used to record information about an Internet user when the user visits websites. Cookies may be useful or desirable by allowing personalization and other time-saving techniques. Many websites require that cookies be enabled to allow the user to connect.
Adware and Popups (15.3.4)
Adware is a form of spyware that is used to collect information about a user based on websites the user visits. That information is then used for targeted advertising. Adware is commonly installed by a user in exchange for a “free” product. When a user opens a browser window, adware can start new browser instances that attempt to advertise products or services based on the surfing practices of the user. The unwanted browser windows can open repeatedly and can make surfing the Internet very difficult, especially with slow Internet connections. Adware can be very difficult to uninstall.
Popups and pop-unders are additional advertising windows that display when a website is visited. Unlike adware, popups and pop-unders are not intended to collect information about the user and are typically associated only with the website being visited.
- Popups—These open in front of the current browser window.
- Pop-unders—These open behind the current browser window.
They can be annoying and usually advertise products or services that the user does not want.

