Objectives
Upon completion of this chapter, you will be able to answer the following questions:
- What are the different types of network security threats?
- What are social engineering attacks?
- What are the various types of malicious software?
- What are denial-of-service attacks?
- How do security tools and software updates mitigate network security threats?
- How does antimalware software mitigate data loss and service disruptions?
Key Terms
This chapter uses the following key terms. You can find the definitions in the Glossary.
denial-of-service (DoS) attack page 308
distributed denial of service (DDoS) page 309
Introduction (15.0.1)
When you leave your home, do you make sure to lock all of your doors? What about your windows? A burglar who really wants to get into your home will check every possible way to do so; therefore, you must be vigilant. It‛s the same with your connected devices and your network. There are many ways that a threat actor can gain access to your network and the information on your devices. In this chapter, you learn more about these attacks and how to thwart them.
Security Threats (15.1)
Whether wired or wireless, computer networks are essential to everyday activities. Individuals and organizations alike depend on their computers and networks for functions such as email, accounting, organization, and file management. Intrusion by an unauthorized person can result in costly network outages and loss of work. Attacks to a network can be devastating and can result in a loss of time and money due to damage or theft of important information or assets.
Types of Threats (15.1.1)
Intruders can gain access to a network through software vulnerabilities, hardware attacks, or even through less high-tech methods, such as guessing usernames and passwords. Intruders who gain access by modifying software or exploiting software vulnerabilities are often called threat actors.
When a threat actor gains access to a network, four types of threats may arise:
- Information theft is breaking into a computer to obtain confidential information. Information can be used or sold for various purposes such as when someone is stealing proprietary information of an organization, like research and development data.
- Data loss or manipulation is breaking into a computer to destroy or alter data records. An example of data loss is a threat actor sending a virus that reformats a computer hard drive. An example of data manipulation is breaking into a records system to change information, such as the price of an item.
- Identity theft is a form of information theft where personal information is stolen for the purpose of taking over someone‛s identity. Using this information, a threat actor can obtain legal documents, apply for credit, and make unauthorized online purchases. Identity theft is a growing problem costing billions of dollars per year.
- Disruption of service is preventing legitimate users from accessing services to which they are entitled. Examples include denial-of-service (DoS) attacks on servers, network devices, or network communications links.
Internal and External Threats (15.1.2)
Security threats from network intruders can come from both internal and external sources, as shown in Figure 15-1.
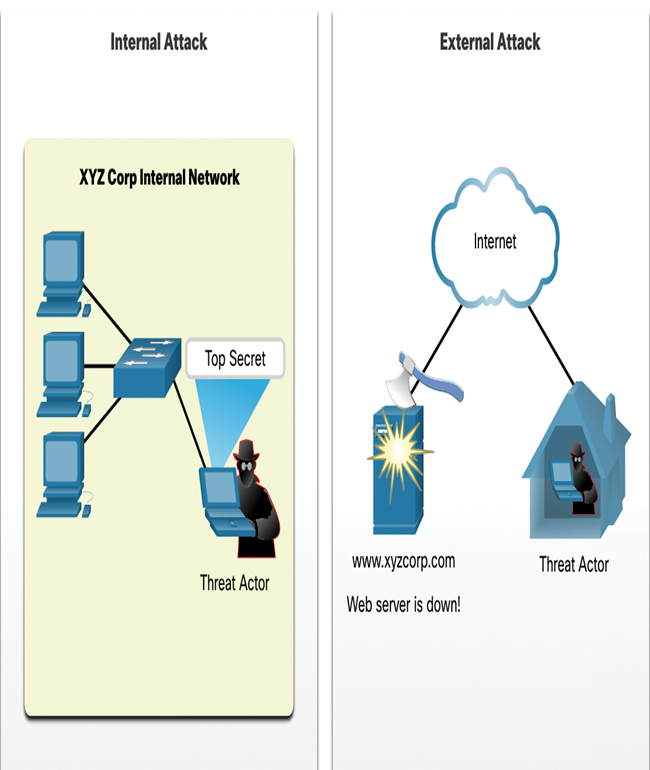
Figure 15-1 Internal and External Attacks
Internal Threats
Internal threats occur when someone has authorized access to the network through a user account or has physical access to the network equipment. Internal attackers know the internal politics and people. They often know what information is both valuable and vulnerable, and how to get to it.
However, not all internal attacks are intentional. In some cases, an internal threat can come from a trustworthy employee who picks up a virus or security threat while outside the company and unknowingly brings it into the internal network.
Most companies spend considerable resources defending against external attacks; however, some of the most damaging incidents are the result of actions by trusted internal users. Lost smartphones and removable storage devices, misplaced or stolen laptops, and the failure to properly remove data from devices before disposal are common ways that user data ends up in the hands of the wrong people.
External Threats
External threats arise from individuals working outside of an organization. They do not have authorized access to the computer systems or network. External attackers work their way into a network mainly from the Internet through wireless links or dial-up access servers.
Social Engineering Attacks (15.2)
One of the easiest ways for an intruder to gain access, whether internal or external, is by exploiting human behavior. One of the more common methods of exploiting human weaknesses is called social engineering.
Overview of Social Engineering (15.2.1)
Social engineering refers to the ability of something or someone to influence the behavior of a person or group of people. In the context of computer and network security, social engineering refers to a collection of techniques used to deceive internal users into performing specific actions or revealing confidential information.
With these techniques, the attacker takes advantage of unsuspecting legitimate users to gain access to internal resources and private information, such as bank account numbers or passwords.
Social engineering attacks exploit the fact that users are generally considered one of the weakest links in security, as shown in Figure 15-2. Social engineers can be internal or external to the organization, but most often do not come face to face with their victims.

Figure 15-2 User as the Weakest Link in Security
Types of Social Engineering Attacks (15.2.2)
Three of the most common methods threat actors use to obtain information directly from authorized users go by unusual names: pretexting, phishing, and vishing.

