In addition to web services, another common service used across the Internet is one that allows users to transfer files.
File Transfer Protocol (12.4.1)
In addition to web services, another common service used on networks is one that allows users to transfer files. The File Transfer Protocol (FTP) provides an easy method to transfer files from one computer to another. A host running FTP client software can access an FTP server to perform various file management functions including file uploads and downloads.
The FTP server enables a client to exchange files between devices. It also enables clients to manage files remotely by sending file management commands such as delete or rename. To accomplish this, the FTP service uses two different ports to communicate between client and server.
The example in Figure 12-4 illustrates how FTP operates. To begin an FTP session, control connection requests are sent to the server using destination TCP port 21. When the session is opened, the server uses TCP port 20 to transfer the data files.
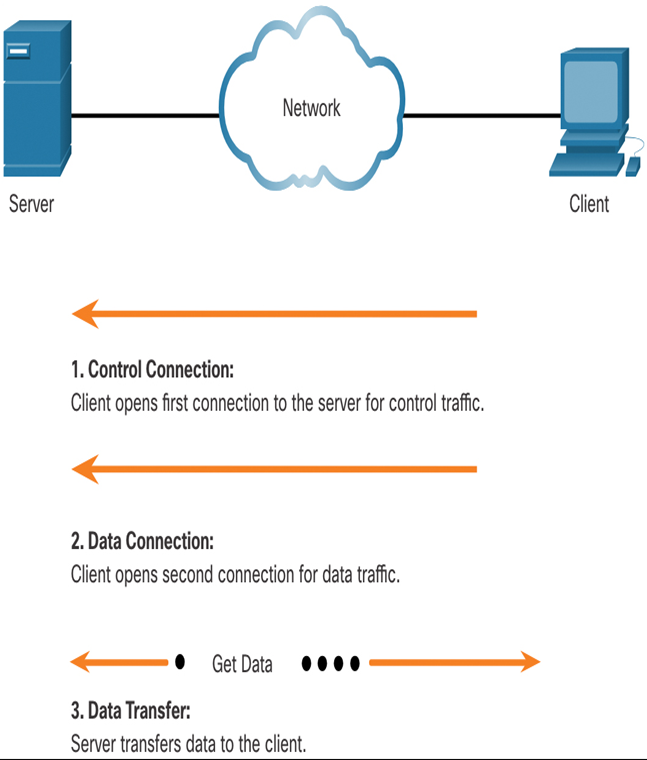
Figure 12-4 FTP Operation
FTP client software is built into computer operating systems and into most web browsers. Standalone FTP clients offer many options in an easy-to-use GUI-based interface.
Video—FTP Client Software (12.4.2)
Refer to the online course to view this video.
FTP Client Software (12.4.3)
Most client operating systems such as Windows, macOS, and Linux include a command-line interface for FTP. There is also GUI-based FTP client software that provides a simple drag-and-drop interface for FTP. After logging in to an FTP server with a username and password, you drag files between the local host window and the remote site (FTP server) window to transfer files.
Figure 12-5 shows FileZilla, the open-source FTP client software.
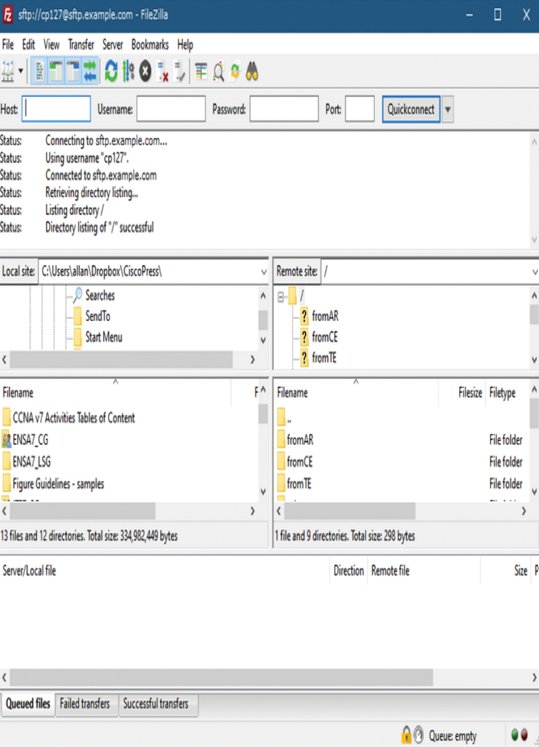
Figure 12-5 FileZilla FTP Client Software
Packet Tracer—Use FTP Services (12.4.4)
In this activity, you will put a file on an FTP server and get a file from an FTP server.
Virtual Terminals (12.5)
Long before desktop computers with sophisticated graphical interfaces existed, people used text-based systems that were often just display terminals physically attached to a central computer. After networks became available, people needed a way to remotely access the computer systems in the same manner that they did with the directly attached terminals.
Video—Remote Access with Telnet or SSH (12.5.1)
Refer to the online course to view this video.
Telnet (12.5.2)
Telnet was developed to meet the need to remotely access computer systems. It dates back to the early 1970s and is among the oldest of the application layer protocols and services in the TCP/IP suite. Telnet provides a standard method of emulating text-based terminal devices over the data network. Both the protocol itself and the client software that implements the protocol are commonly referred to as Telnet. Telnet servers listen for client requests on TCP port 23.
Appropriately enough, a connection using Telnet is called a virtual terminal (vty) session, or connection. Rather than using a physical device to connect to the server, Telnet uses software to create a virtual device that provides the same features of a terminal session with access to the server‛s command-line interface (CLI).
In Figure 12-6, the client has remotely connected to the server via Telnet. The client is now able to execute commands as if it were locally connected to the server.
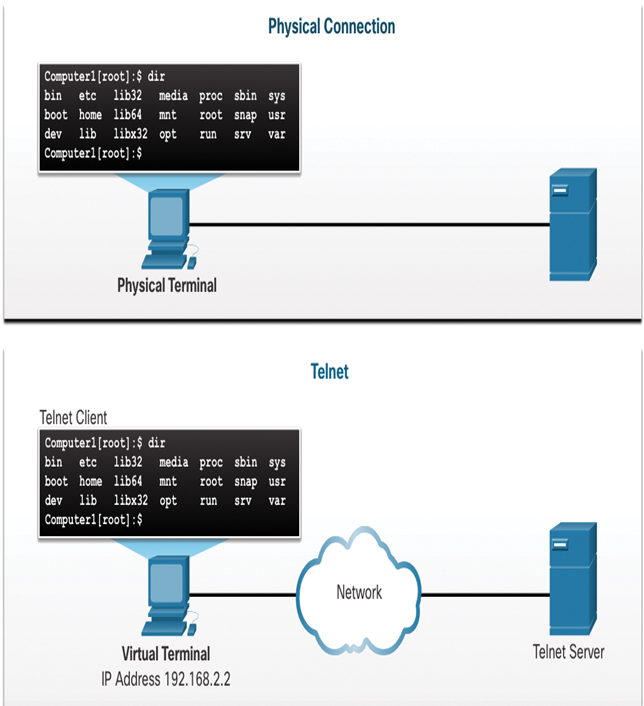
Figure 12-6 Client Remotely Accessing a Server
Note
Telnet is not considered to be a secure protocol. SSH should be used in most environments instead of Telnet. Telnet is used in several examples in this course for simplicity of configuration.
Security Issues with Telnet (12.5.3)
After a Telnet connection is established, users can perform any authorized function on the server, just as if they were using a command-line session on the server itself. If authorized, they can start and stop processes, configure the device, and even shut down the system.
Although the Telnet protocol can require a user to log in, it does not support transporting encrypted data. All data exchanged during Telnet sessions is transported as plaintext across the network. This means that the data can be easily intercepted and understood.
The Secure Shell (SSH) protocol offers an alternate and secure method for server access. SSH provides the structure for secure remote login and other secure network services. It also provides stronger authentication than Telnet and supports transporting session data using encryption. As a best practice, network professionals should always use SSH in place of Telnet, whenever possible.
Figure 12-7 illustrates how SSH is more secure than Telnet. Notice how the data captured by the hacker when Telnet is used is clearly readable, whereas the data captured when SSH is used is encrypted and therefore more secure.
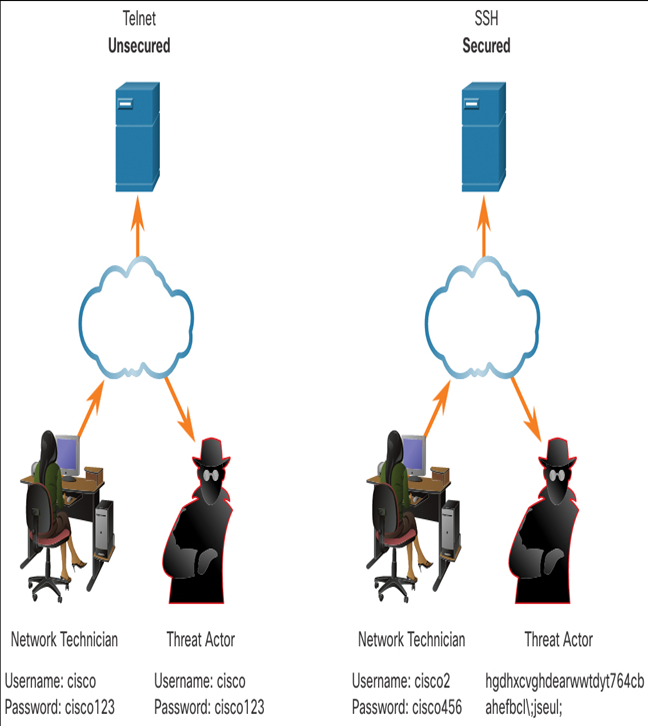
Figure 12-7 Telnet and SSH Comparison
Packet Tracer—Use Telnet and SSH (12.5.4)
In this activity, you will establish a remote session to a router using Telnet and SSH.

